This might be helpful for people like me who recently started learning Postfix:
If you want to eliminate the “red padlock” icon in Gmail, you do not need to get a certificate. Mail servers like Gmail don’t require you to have a certificate (aka client certificate) to connect to them over a secure TLS connection, and subsequently send mail to them (however, things like SPF TXT records and DKIM are needed to avoid Gmail marking your mail as spam).
To send mail to Gmail (and others) with TLS and get rid of the “red padlock”, you only need:
smtp_tls_security_level = may
smtp_tls_loglevel = 1
smtp_tls_CAfile = /etc/ssl/certs/ca-certificates.crt
…in /etc/postfix/main.cf
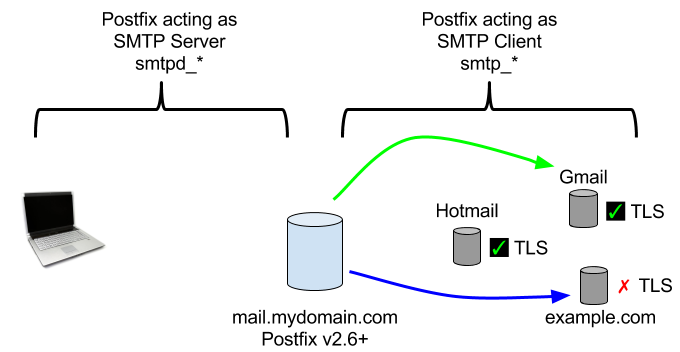
TLS-security-level “may” (“You *may* use TLS”) means your mail will be relayed even if the other mail server lacks TLS. This is represented by the BLUE arrow in the diagram showing mail sent to “example.com”. In other words, such mail will be sent unencrypted, but it will successfully reach example.com.
“smtp_*” are the parameters for the Postfix SMTP Client (the code that talks to public Internet mail servers like Gmail’s mail servers). The “smtpd_*” parameters are for the Postfix SMTP Server (the code that your users connect to when they need to send email to Gmail or some other public Internet mail server).
Make sure ca-certificates.txt exists in postfix’s chroot “jail” (on my ubuntu server it was: /var/spool/postfix/etc/ssl/certs/ca-certificates.crt). This is a database of certs of well-known CAs that your postfix server needs to know when it connects to Gmail (or other mail server). When your postfix server connects to Gmail, Gmail will present to postfix *Gmail’s server cert*, and that server cert will be signed by one of these well-known CAs.
I’m running postfix 2.11.0 on ubuntu 14.04.
You may configure smtp_tls_ciphers and smtp_tls_protocols, but the defaults are OK and recommended. The default for smtp_tls_ciphers is ‘medium’. If you do ‘high’, there’s a (small) chance some of your mail won’t reach destinations that don’t support the strongest ciphers. The default for smtp_tls_protocols is ‘!SSLv2, !SSLv3’ (disable SSL v2 and v3), which is considered safe; it allows TLSv1.
Svenn (https://www.svennd.be) wrote very helpful articles about how to use LetsEncrypt. Such certs are needed when *your* remote users (email clients) need to connect to your postfix server over a secure TLS connection. That’s another article.